Two Factor Authentication? That’s so half a decade ago! Now we have 5-Factor Authentication (I have no idea how I am supposed to deal with it, frankly). All around the internet, I have only read titles saying good things about it, so let’s dive in together and see what the fuss is all about.
What is 5-Factor Authentication and How Does it Work?
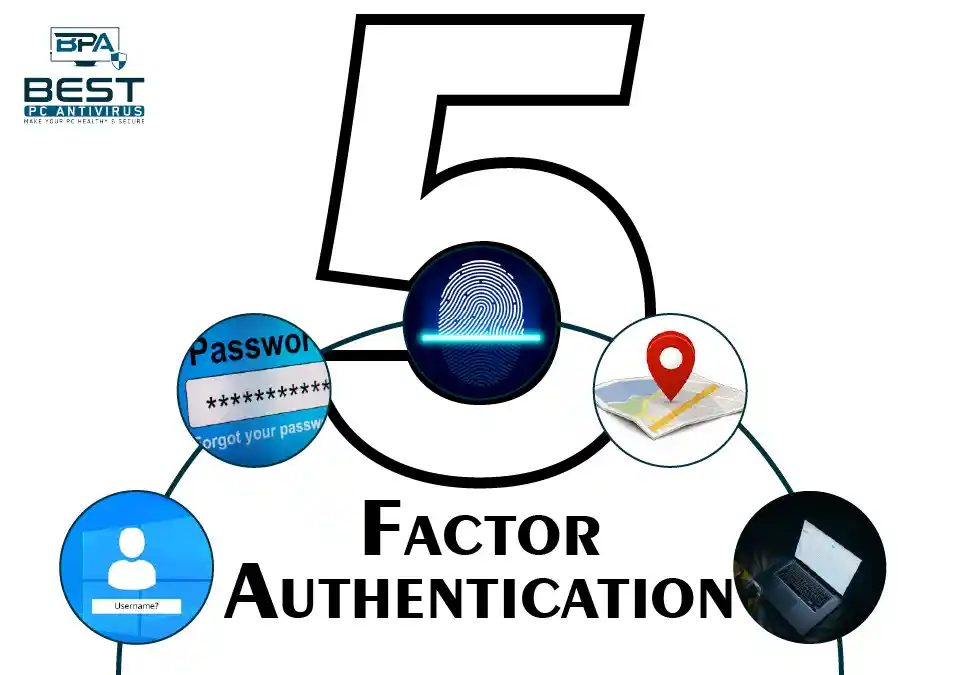
Five-factor authentication (5FA) is an advanced security measure that adds an additional layer of security to the traditional authentication methods, such as passwords, biometric identification, and smart cards. 5FA requires users to provide five distinct authentication factors to gain access to a system or device, providing an even higher level of security than traditional multi-factor authentication (MFA) methods.
The five factors of authentication in 5FA are:
- Something you know: This factor refers to information that only the user should know, such as a password or PIN. It is the most common authentication factor used in traditional authentication methods.
- Something you have: This factor refers to something physical that the user possesses, such as a smart card or a security token. It provides an extra layer of security because a hacker would need to physically steal the device to gain access.
- Something you are: This factor refers to biometric authentication, such as facial recognition, iris scan, or fingerprint authentication. Biometric authentication is considered to be highly secure because it is difficult to replicate.
- Somewhere you are: This factor refers to geolocation authentication, which uses GPS technology to determine the user’s location. It can help prevent unauthorized access from remote locations.
- Something you do: This factor refers to behavioral authentication, which analyzes the user’s behavior and habits, such as typing speed or mouse movements. It is often used in combination with other authentication factors to add an additional layer of security.
To use 5FA, the user is required to provide all five authentication factors during the login process. The system will then verify each factor and grant access only if all five factors are verified successfully. For example, the user might be required to enter a password (something they know), insert a security token (something they have), perform a facial recognition scan (something they are), be physically present in a particular location (somewhere they are), and complete a certain mouse movement pattern (something they do). If any of the factors fail to be verified, the user will not be granted access.
The benefits of 5FA are obvious: it provides an even higher level of security than traditional authentication methods. However, it is also more complex and can be more time-consuming for users to complete, which may cause frustration or resistance. 5FA is typically used in high-security situations where the data or system being protected is particularly sensitive, such as in military or government organizations, financial institutions, or healthcare organizations.
Understanding the Benefits of 5-Factor Authentication
Five-factor authentication (5FA) is an advanced security measure that adds an additional layer of security to traditional authentication methods, such as passwords, biometric identification, and smart cards. By requiring users to provide five distinct authentication factors to gain access to a system or device, 5FA provides an even higher level of security than traditional multi-factor authentication (MFA) methods.
Some of the key benefits of 5FA are:
- Increased Online Security Levels: With the growing number of cyberattacks and data breaches, online security has become a major concern for individuals and businesses. 5FA provides a higher level of security than traditional authentication methods, making it more difficult for hackers to gain access to sensitive data or systems.
- Secure Online Transactions: Online transactions involving sensitive financial or personal data require a high level of security to prevent fraud or identity theft. 5FA provides an additional layer of security, ensuring that only authorized users can access the data and perform the transaction.
- Secure Data Storage: Data storage is another area where 5FA can be particularly useful. By requiring five different authentication factors to access data, it becomes much more difficult for hackers to steal or corrupt the data, ensuring that it remains secure and confidential.
- Secure User Access: User access to sensitive systems or data can be tightly controlled with 5FA. By requiring users to provide multiple authentication factors, it becomes much more difficult for unauthorized users to gain access to the system or data.
- Improved Compliance: Many industries and government regulations require a high level of security for certain types of data, such as healthcare information or financial data. By implementing 5FA, businesses can improve their compliance with these regulations and avoid costly fines and penalties.
5FA provides an additional layer of security for sensitive data and systems, ensuring that only authorized users can access them. While it may be more complex and time-consuming than traditional authentication methods, the benefits of 5FA make it a valuable security measure for businesses and individuals alike.
How to Implement a Secure 5-Factor Authentication System
Implementing a secure 5-factor authentication (5FA) system requires careful planning and execution to ensure that the system is both effective and user-friendly. Here are some key steps to consider when implementing a 5FA system:
- Evaluate your security needs: Determine what level of security you require and what data or systems need to be protected. This will help you determine what authentication factors to include in your 5FA system.
- Choose the right authentication factors: Select authentication factors that are both secure and easy for users to use. Consider factors such as passwords, security tokens, biometric authentication, geolocation, and behavioral authentication.
- Setup a multi-factor authentication system: Setting up a multi-factor authentication system involves integrating the chosen authentication factors into a single system. You will need to consider the user interface, how to store and manage the authentication data, and how to integrate the system with your existing security protocols.
- Develop a security protocol: Develop a comprehensive security protocol that outlines how the 5FA system will be used, who has access to it, and how it will be maintained and updated.
- Train users: Provide thorough training for users on how to use the 5FA system effectively and securely. This will help ensure that the system is used correctly and that users understand the importance of the additional security measures.
- Implement biometric authentication: Biometric authentication is one of the most secure authentication factors available, but it requires careful planning and execution. Consider the type of biometric authentication to use, such as fingerprint or facial recognition, and ensure that the system is secure and accurate.
- Test and monitor the system: Test the 5FA system thoroughly before implementing it and monitor it closely to ensure that it is working effectively and that any issues are addressed promptly.
Different Types of Authenticators in a Multi-Factor System
A multi-factor authentication (MFA) system requires users to provide multiple authentication factors in order to gain access to a system or device. There are several different types of authenticators that can be used in a multi-factor authentication system, including:
- Passwords: Passwords are the most commonly used authentication factor. They require users to enter a unique password that is associated with their account. While passwords are a convenient and widely-used authentication factor, they can be vulnerable to hacking and phishing attacks.
- Security Tokens: Security tokens are small hardware devices that generate a one-time password (OTP) that is used for authentication. The OTP changes frequently, making it difficult for hackers to guess or intercept the code.
- Biometric Authentication: Biometric authentication uses a person’s unique physical characteristics, such as their fingerprint, face, or voice, to verify their identity. Biometric authentication is highly secure, as it is difficult for anyone else to replicate a person’s biometric data.
- Smart Cards: Smart cards are similar to security tokens, but they are embedded with a microprocessor that can store and process data. They require users to insert the card into a card reader in order to authenticate their identity.
- Push Notifications: Push notifications are used for mobile authentication and involve sending a notification to the user’s mobile device, which they must approve to gain access to the system.
- Password Manager: A password manager is a software program that stores all the user’s passwords in an encrypted format. The user only has to remember one master password to access the password manager. The password manager can generate strong, unique passwords for each account, making it more difficult for hackers to gain access to multiple accounts.
Each type of authenticator has its own strengths and weaknesses, and the most secure multi-factor authentication systems typically use a combination of different authenticators to provide the highest level of security.
Why You Should Consider Introducing 5-Factor Authentication to Your Online Platforms and Services
In today’s digital age, cybersecurity threats are more prevalent than ever, and the need for strong authentication measures is crucial. Introducing a 5-factor authentication (5FA) system can significantly enhance the security of your online platforms and services, providing an extra layer of protection against unauthorized access.
The use of multiple authentication factors, including passwords, security tokens, biometric authentication, geolocation, and behavioral authentication, can make it more difficult for hackers to gain access to sensitive data and systems. By implementing a 5FA system, you can improve the overall security of your organization and protect your customers’ sensitive information.
In addition to the security benefits, 5FA systems can also improve the user experience by reducing the need for complex and cumbersome passwords. With the use of biometric authentication and other user-friendly authentication factors, users can log in to their accounts quickly and easily, without sacrificing security.
Overall, the implementation of a 5FA system is a smart investment in the protection of your organization’s data and assets. By using multiple authentication factors, you can significantly reduce the risk of cybersecurity threats and provide a more secure and convenient user experience for your customers.
FAQs
What is 5-Factor Authentication and how does it work?
Five-Factor Authentication (5FA) is an advanced security measure that adds an additional layer of security to traditional authentication methods, such as passwords, biometric identification, and smart cards. It requires users to provide five distinct authentication factors to gain access to a system or device, providing a higher level of security than traditional multi-factor authentication (MFA) methods. The five factors of authentication in 5FA are: Something you know, Something you have, Something you are, Somewhere you are, and Something you do.
What are the benefits of 5-Factor Authentication?
Some of the key benefits of 5FA are increased online security levels, secure online transactions, secure data storage, secure user access, and improved compliance. 5FA provides an additional layer of security for sensitive data and systems, ensuring that only authorized users can access them. By requiring users to provide multiple authentication factors, it becomes much more difficult for unauthorized users to gain access to the system or data.
What are the key steps to consider when implementing a 5-Factor Authentication system?
The key steps to consider when implementing a 5FA system are to evaluate your security needs, choose the right authentication factors, set up a multi-factor authentication system, develop a security protocol, and train users. Implementing a secure 5FA system requires careful planning and execution to ensure that the system is both effective and user-friendly.
What are the five factors of authentication in 5-Factor Authentication?
The five factors of authentication in 5FA are: Something you know, Something you have, Something you are, Somewhere you are, and Something you do. These factors refer to information that only the user should know, something physical that the user possesses, biometric authentication, geolocation authentication, and behavioral authentication, respectively.
Why is 5-Factor Authentication considered a valuable security measure for businesses and individuals alike?
5FA provides an additional layer of security for sensitive data and systems, ensuring that only authorized users can access them. While it may be more complex and time-consuming than traditional authentication methods, the benefits of 5FA make it a valuable security measure for businesses and individuals alike. It offers increased online security levels, secure online transactions, secure data storage, secure user access, and improved compliance.
Read More : Guide : Cybersecurity for Marketing Organizations