The education sector / educational sector is facing a growing and intricate cybersecurity problem. Educational institutions are being…
Conversation Hijacking and How to Deal With It
Conversation Hijacking is becoming more and more prevalent these days. You might not even have heard about this…
How AI Can Leak Your Private Data
Utilizing technology such as AI can often lead to inadvertent or unwilling exposure of private data, such as…
Bringing Cyber Safety to Esports
All of the mums on this planet, including me, are worried about this topic. Y’all on the other…
Introducing “5-Factor Authentication”
Two Factor Authentication? That’s so half a decade ago! Now we have 5-Factor Authentication (I have no idea…
Norton 360 Antivirus review (2023)
Norton’s 360 security suite has been widely recognized as one of the most superior antivirus programs in 2023.…
Cybersecurity Guide: Securing the Marketing Sector
The majority of today’s marketing professionals dedicate a considerable portion of their time online. However, conducting business on…
Session hijacking : What is session hijacking and how does it work?
What is Session Hijacking? The best and the simplest way in which I can explain it to you…
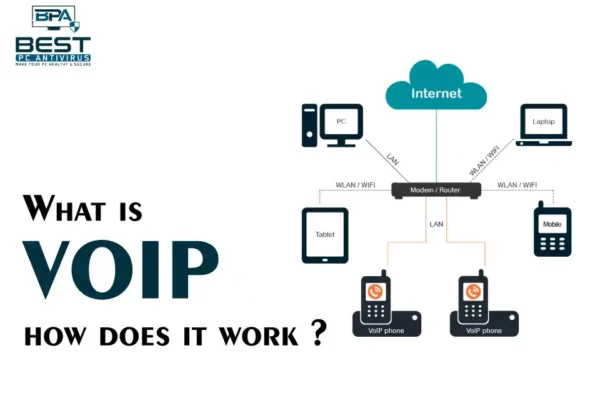
What is Voice over Internet Protocol and How Does it Work
To begin with, VOIP stands for Voice over Internet Protocol. It is basically a technology that allows voice…
When Spyware Arrives From Someone You Trust
If you are sharing your digital space with someone, or are close with a potential murderer, it may…